
Back to School Technology: Are You Ready?
July 7, 2020
Most districts and states have begun working through the logistics of returning to school for faculty, staff, and students. Many lessons were learned over the spring and early summer about how to implement distance education and working from home. However, access and digital security issues remain. Unfortunately, these issues will not be resolved unless we take in the entire landscape of making the digital connection from students to instructors in a virtual environment. Below are some things to consider.
 IT Auditing
IT Auditing
IT auditing includes the tracking, via software, of computer hardware, associated devices, and software. This is increasingly valuable as students, faculty, and staff are working from home and using products purchased by states and school districts. Typically, devices are equipped with a bar code or other coding system if they are above a cost threshold, these items can be manually tracked with a bar code scanner or within a database. A newer tool, tracking software with Internet of Things (IoT) capacity, greatly decreases the manual work of finding and scanning individual pieces of equipment by directly broadcasting location information to the tracking software.
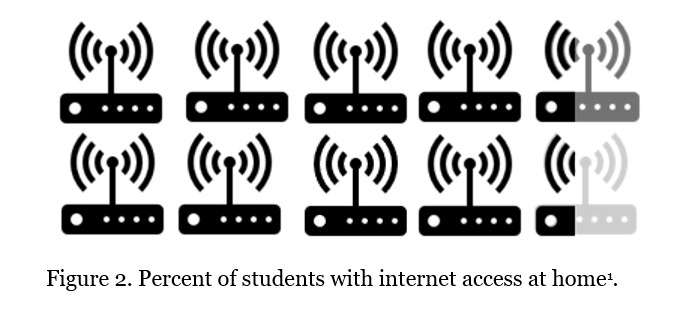
Auditing an entity’s hardware and software is important for insurance, replacement, and maintenance purposes. In 2014, the Office of Audits completed a sample audit of the U.S. Securities and Exchange Commission’s laptops. It was found that from this sample, 17% had incorrect location information, 22% had incorrect user information, and another 5% could not be found[2]. If a laptop costs $300 and a state orders 10,000 of them, this represents a loss of $150,000 in hardware alone.
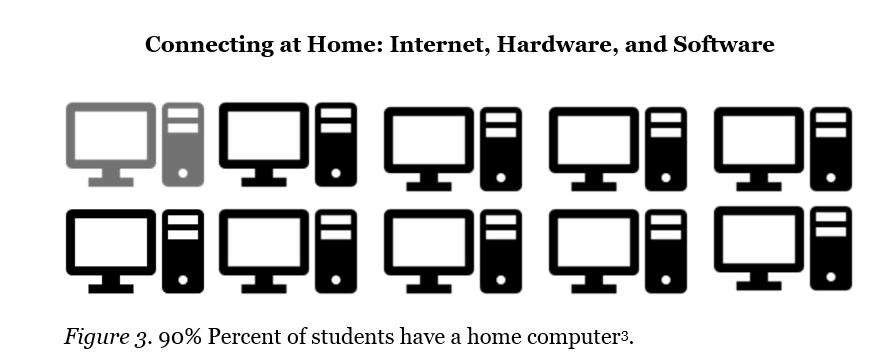
Students, faculty, and staff, while having specific needs, have layers of overlap in the types of technology needed to productively work and learn from home. Needs may include:
- internet access
- wireless hot spots
- batteries
- wireless rollerballs
- joysticks
- keyboards
- tablets/laptops
- protective cases
- tablet carrying bags
- software
All or some of which may be managed by a school, a district, a state government, a nonprofit, or a contracted service provider. However, it is important to note that simply having internet does not mean that it is highspeed or able to support multiple users at once. Similarly, having a computer in the household does not mean that is compatible with the needed learning platforms and multiple people may be sharing a single machine.
Hot spot use: Generally battery-operated, hot spots are purchased with a data plan from a wireless provider. This is connected as a Wi-Fi signal to the selected device. The benchmark price is $124 per unit and ranges from $25 to >$3300 depending on factors such as durability and range4. The average range is approximately 120 feet.
Specifically, internet access is a challenge because of the need for either a 4G LTE connection or an internet service provider (ISP) to have cables installed in an area. Rural areas may have neither due to factors including terrain and population density. Options for students, faculty, and staff who live in rural areas without an LTE connection or an ISP may include:
service provider (ISP) to have cables installed in an area. Rural areas may have neither due to factors including terrain and population density. Options for students, faculty, and staff who live in rural areas without an LTE connection or an ISP may include:
Satellite internet service: requires the use of a satellite dish, satellite internet modem, and line of sight to the service’s satellite. Benchmark pricing is approximately $100/month and varies with internet speed[4].
Or
Fixed Wireless internet service: requires the installation of a long-range antenna, router, line of sight to the service’s fixed wireless hub or tower.
Cloud Computing Services
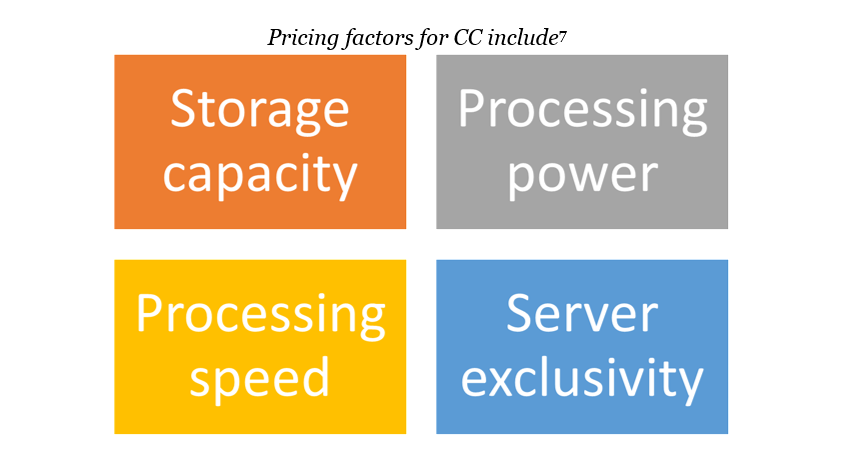
Cloud computing is a tool for storing data and software on a shared server[5]. Cloud computing (CC) is scalable and can be controlled by the user via metering. The benefits of using CC services include[6]:

The formatting structures are flexible, allowing for the instructor to readily change content and visual components. The ability of CC to be scalable is important because the number of people accessing it may vary widely over the course of a day. Most CC services are maintained by a third party, thus decreasing the cost for maintenance, and reducing the need for hard copies of software. Collaborative learning is quick and easy using CC, and students can meet in real time or asynchronously. Finally, virtual reality opportunities exist in the form of 3-D field trips or robotics and engineering applications.
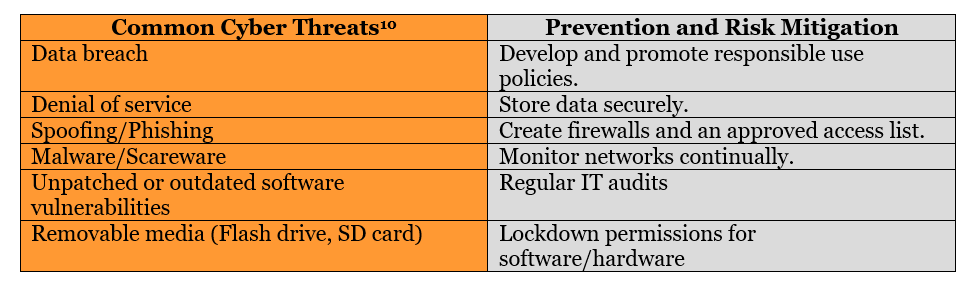
Cyber Security and Risk Mitigation
Working remotely entails the risk of a data breach. Security is a top concern for state agencies[8]. Cyber-attacks on government servers at all levels proliferate[9]
Schools and agencies must be prepared to continually train students, faculty, staff, and parents about the risks of digital access and ways they reduce the risk of a breach. The Readiness and Emergency Management for Schools, Technical Assistance Center (REMS TA Center), administered by the Department of Education and the Office of Safe and Supportive Schools, offers both a comprehensive website and specific guidance on cybersecurity considerations for K-12 schools and school districts.
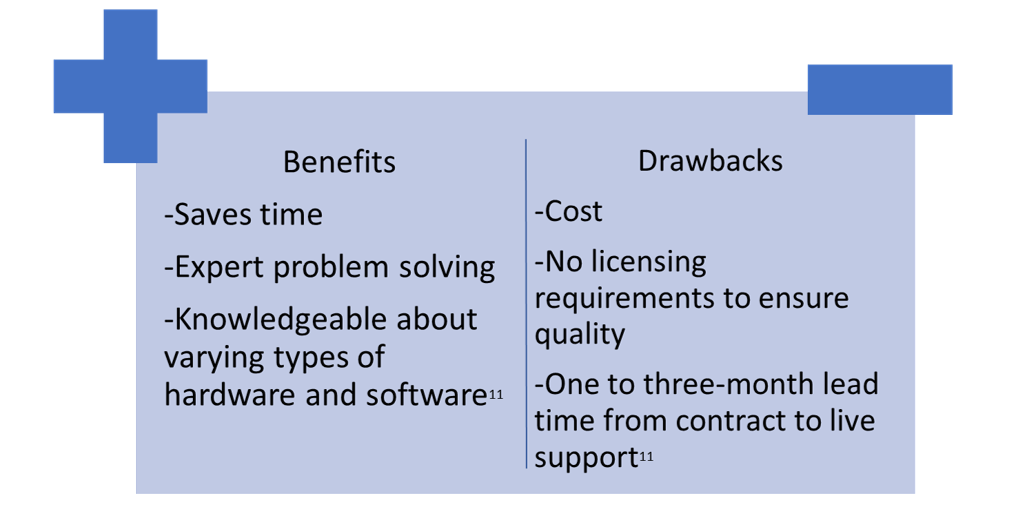
IT Support
IT support works behind the scenes to make sure that software and/or hardware is correctly working every time it is used. Whether technology support is in-house or managed by a provider, they are a critical component of a well-rounded accessibility plan.
Think about Exceptional Children
Students who may need additional tools include students with:

The links below contain classroom software, hardware, and assistive technologies needed for exceptional children. Examples of these include: text to speech software, visually impaired accessible e-books, and phonetic spelling software, among others.
The Resource Library from the Educating All Learners Alliance
Resources for Teaching Remotely from the Council for Exceptional Children
COVID-19 Information and Resource for Schools and School Personnel from the U.S. Department of Education
[1] National Center for Education Statistics. (2020, May). Children’s internet access at home. Retrieved on June 24, 2020, from https://nces.ed.gov/programs/coe/indicator_cch.asp#f2.
[2]U.S. Securities and Exchange Commission, Office of Inspector General, Office of Audits. (2014, September 22). Controls over the SEC’s inventory of laptop computers. Retrieved on June 25, 2020, from https://www.sec.gov/files/524.pdf.
[3] National Center for Education Statistics. (2019, December). Digest of education statistics: 2018. Retrieved on June 24, 2020, from https://nces.ed.gov/programs/digest/d18/index.asp.
[4] Federal Communications Commission. (2020, February 5). Getting broadband q&a. Retrieved on June 24, 2020, from https://www.fcc.gov/consumers/guides/getting-broadband-qa.
[5] Mell, P. & Grance, T. (2011, September). The NIST definitions of cloud computing: Recommendations of the National Institute of Standards and Technology. Retrieved on June 22, 2020 from https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf.
[6] Qasem, Y. A., Abdullah, R., Jusoh, Y. Y., Atan, R., & Asadi, S. (2019). Cloud Computing Adoption in Higher Education Institutions: A Systematic Review. IEEE Access, 7, 63722-63744.
[7] Procurement IQ. (2020, March). IT hosting services. Retrieved June 22, 2020, from https://rb.gy/uywa5p.
[8] The Exchange. (2019, September 18). Cybersecurity challenges for state and local government. New Hampshire Public Radio. https://www.nhpr.org/post/cybersecurity-challenges-state-and-local-government#stream/0
[9] UNITED STATES. COUNCIL OF ECONOMIC ADVISORS, & United States. President. (1947). The Economic Report of the President. Government Printing Office.
[10] Readiness and Emergency Management for Schools, Technical Assistance Center. (nd). Cybersecurity considerations for K-12 schools and school districts. Retrieved June 23, 2020, from https://rems.ed.gov/REMSPublications.aspx.
[11] Deschaine, M. (2018). Supporting students with disabilities in k-12 online and blended learning. Lansing, MI: Michigan Virtual University. Retrieved from https://mvlri.org/research/publications/supporting-students-with-disabilities-in-k-12-online-and-blended-learning/
