Improving Cybersecurity in State Procurement
May 25, 2021
Technology is increasingly connected through cloud infrastructure making it more efficient and accessible, however more risk is taken on.[1] States are migrating to Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS) solutions. The information and functionality of cloud-based state systems contain very sensitive material, in the event of a breach, it could be catastrophic. Expanding cyberattack vulnerabilities such as remote work, Internet of Things (IoT),[2] and supply chain[3] increases risk exponentially, and is not just data compromise, but real life implications. Ransomware can hold government funds hostage and halt vital government processes. The disruption can have a huge impact on beneficiaries who depend on these processes for survival. Cyber warfare can cripple an economy through attacks on supply chains and utilities. Critical government operations and IT have a mutually exclusive relationship. Comprehensive security procedures need to meet the demands of the ever-changing landscape of cybersecurity threats.
The threat of cyberattacks has never been higher and the potential fallout has never been more dangerous. The National Association of State Chief Information Officers (NASCIO) states in their 2021 Federal Advocacy Priorities[4] that cybersecurity is no longer an IT issue but one that concerns all levels of government, “The risk poses devastating consequences to functions of society, economy, and national security.” The Center for Internet Security (CIS) produced the 2021 Cybersecurity Trends to Prepare For[5] that features comments from leaders in cyber security to provide trends and forward-thinking strategies.
A recent paper produced as a collaborative effort between from the NASCIO, CIS, and NASPO, Buyer Be Aware – Integrating Cyber Security into the Acquisition Process tackles mitigation strategies such as market research, risk management, and enterprise architecture.
-Buyer Be Aware – Integrating Cyber Security into the Acquisition Process
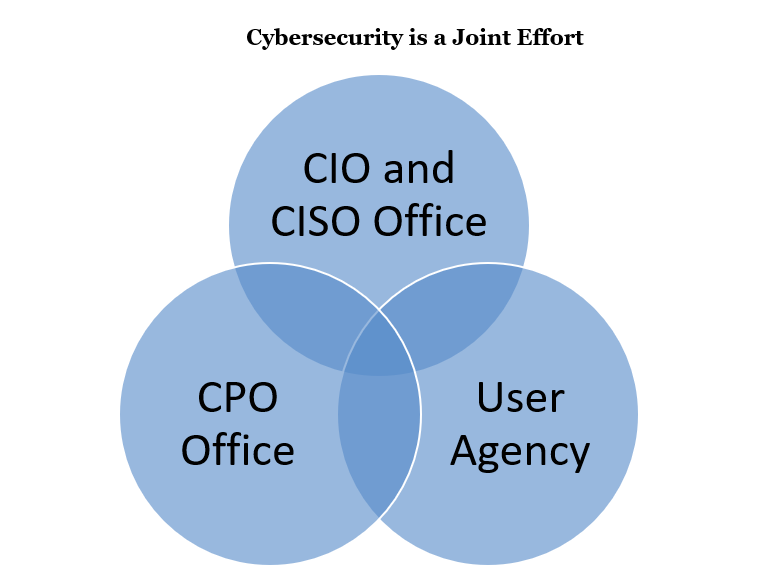
Procurement has been challenged to adapt its processes to meet the demands of agency stakeholders who need new and emerging technology. Procurement statutes may not be current enough to support the procedures that are necessary to acquire rapid solutions. Collaboration starts from the procurement process to contract management, including routine tests and maintenance. It is critical that the Chief Information Officer (CIO), Chief Information Security Officer (CISO), Chief Procurement Officer (CPO), and the user agency work together from the very beginning of the procurement to plan and ensure that cyber security mitigation is incorporated into the agency need. All procurement stakeholders must be able to work together to ensure the safety and security of these technology systems. NASPO recently did a case study on the 2018 George Cronin Award for Procurement Excellence, Bronze and is a great example of early interagency collaboration and innovation.
The battle against cyberattacks is a 24/7 effort, adding to the risk is state data that is inherently sensitive. Cybersecurity has never been in more demand for government entities. The defense practices are daunting, and protocols can change on a moment’s notice. Strong relationships can position joint efforts for continuous preparation and through knowledge sharing to develop mitigation strategies. Though the layer of protection will never be 100%, cybersecurity innovation must be a top priority.
[1] Morrow, T. (2018, March 5). 12 Risks, Threats, & Vulnerabilities in Moving to the Cloud. Carnegie Mellon University’s Software Engineering Institute Blog. http://insights.sei.cmu.edu/blog/12-risks-threats-vulnerabilities-in-moving-to-the-cloud
[2] Brooks,C. (2021, April 12). 3 Key Cybersecurity Trends To Know For 2021 (and On …). Forbes. https://www.forbes.com/sites/chuckbrooks/2021/04/12/3-key-cybersecurity-trends-to-know-for-2021-and-on-/?sh=1eeacf4d4978
[3] Sanger, D., Krauss, C., Perlroth, N. (2021, May 13). Cyberattack Forces a Shutdown of a Top U.S. Pipeline. New York Times. https://www.nytimes.com/2021/05/08/us/politics/cyberattack-colonial-pipeline.html
[4] NASCIO. (2021). Authorize and Appropriate a Dedicated Cybersecurity Grant Program for State and Local Governments. NASCIO 2021 Advocacy Priority. https://www.nascio.org/government-affairs/
[5] CIS. (2021). 2021 Cybersecurity Trends to Prepare For. https://www.cisecurity.org/blog/2021-cybersecurity-trends-to-prepare-for/
